Written by Laurens Slat, Developer Relations, AVSystem

This blog originally ran on the AVSystem website. For more content like this, click here.
As more and more resource-constrained IoT devices are being deployed, firmware updates over the air (FOTA) are becoming increasingly important. As physical access is often expensive, or even impossible to realize when operating large deployments in remote, hard-to-reach locations, FOTA provides the way to fix bugs, patch security vulnerabilities or add functionality throughout the lifespan of a connected device.
The Lightweight M2M standard defines the process for remote firmware updates. When following the standardized guidelines provided by the protocol, updating the firmware of resource-constrained devices can be accomplished effortlessly and securely, regardless of the device or platform used.
The LwM2M way of updating firmware OTA
LwM2M is OMA SpecWork’s response to the ever-growing need for faster, easier and more power-efficient communication. LwM2M is an application-layer communication standard which enables embedded developers to accelerate IoT application development. Rather than implementing communication protocols, security standards or device management functionality, developers can use one of the available (open source) LwM2M Clients which come with all necessary features for building a secure, scalable and interoperable IoT solution.
The LwM2M standard defines a client-server architecture, communication semantics and device management mechanisms including firmware updates over the air. The efficient data format makes it well suited for resource-constrained IoT devices such as low-power microcontrollers using cellular connections.
To realize interoperability, LwM2M uses standardized Objects to represent configurations (e.g., preferred radio technology, security implementation), functionalities (connectivity monitoring, FOTA), and peripherals (temperature, humidity, GPS). No matter the hardware or firmware used, as long as the LwM2M Server knows what Objects the device supports, it can process the data and manage the device remotely.
Popular LwM2M Clients which are built on top of Zephyr are the Zephyr LwM2M Client (maintained by the Zephyr Project) and Anjay (maintained by AVSystem). Both Clients support OTA firmware updates as dictated by the LwM2M specifications.
Firmware update process
Generally speaking, the LwM2M firmware update process consists of four steps:
- The IoT device (referred to as the LwM2M Client) is triggered to initiate the firmware update process.
- The LwM2M Client downloads the firmware and reports to the LwM2M Server when the download is finished.
- The LwM2M Client performs the firmware update after validating the integrity and authenticity of the new firmware which is done through a process called secure boot.
- The Client attempts to run the new firmware and reports the status to the Server. If succeeded, the device starts running the new firmware, if an error is encountered the device performs a rollback to the earlier firmware version.
This procedure is defined in detail in the LwM2M specifications (see LwM2M specifications). To add firmware update capabilities to a device, the Firmware Update Object /5 needs to be implemented containing all essential functionalities for conducting the update and reporting the status. Several LwM2M Clients natively support this Firmware Update Object, including AVSystem’s Anjay and Zephyr’s LwM2M Client.
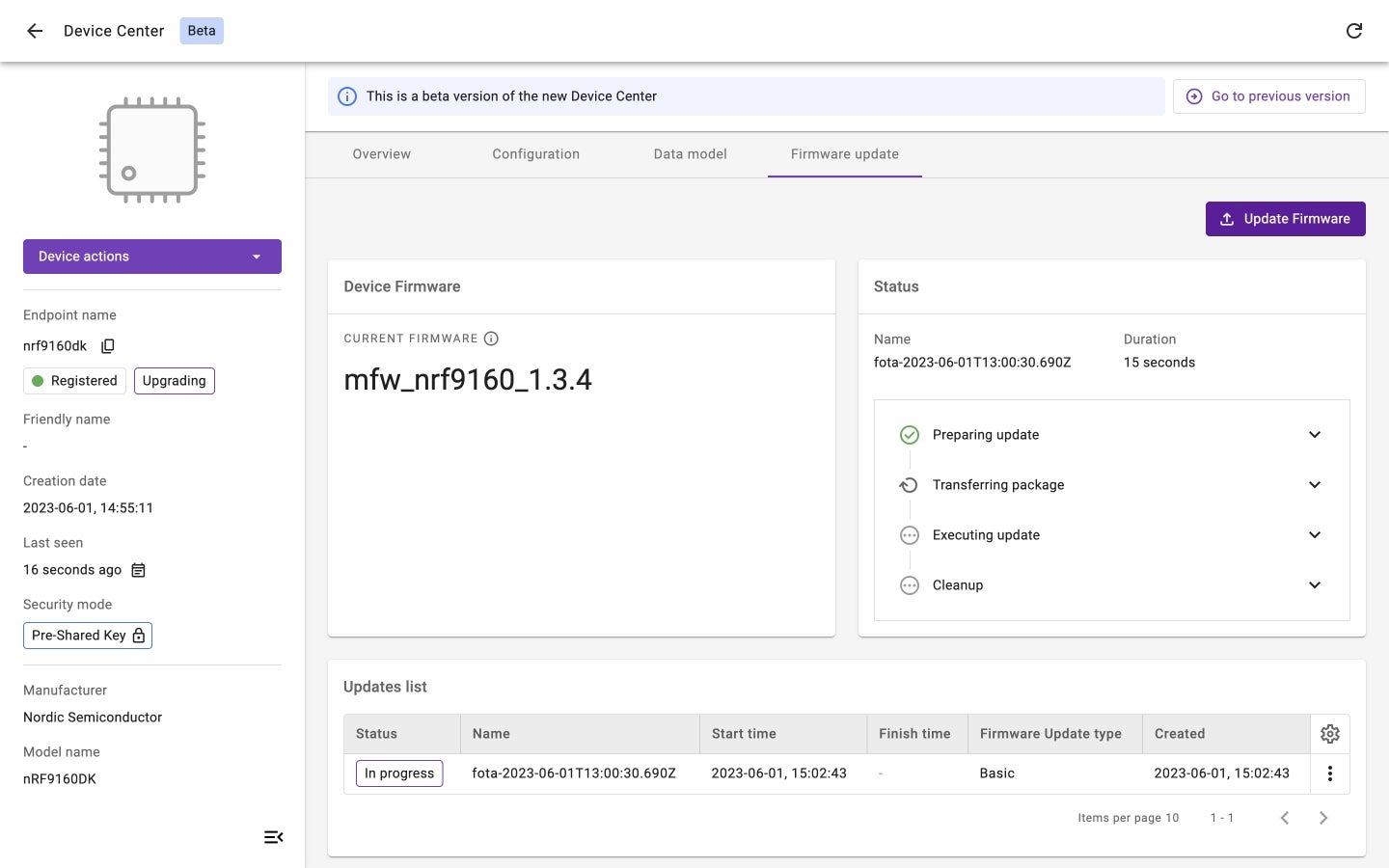
Updating a device’s firmware using AVSystem’s LwM2M Server called Coiote IoT Device Management
Downloading new firmware
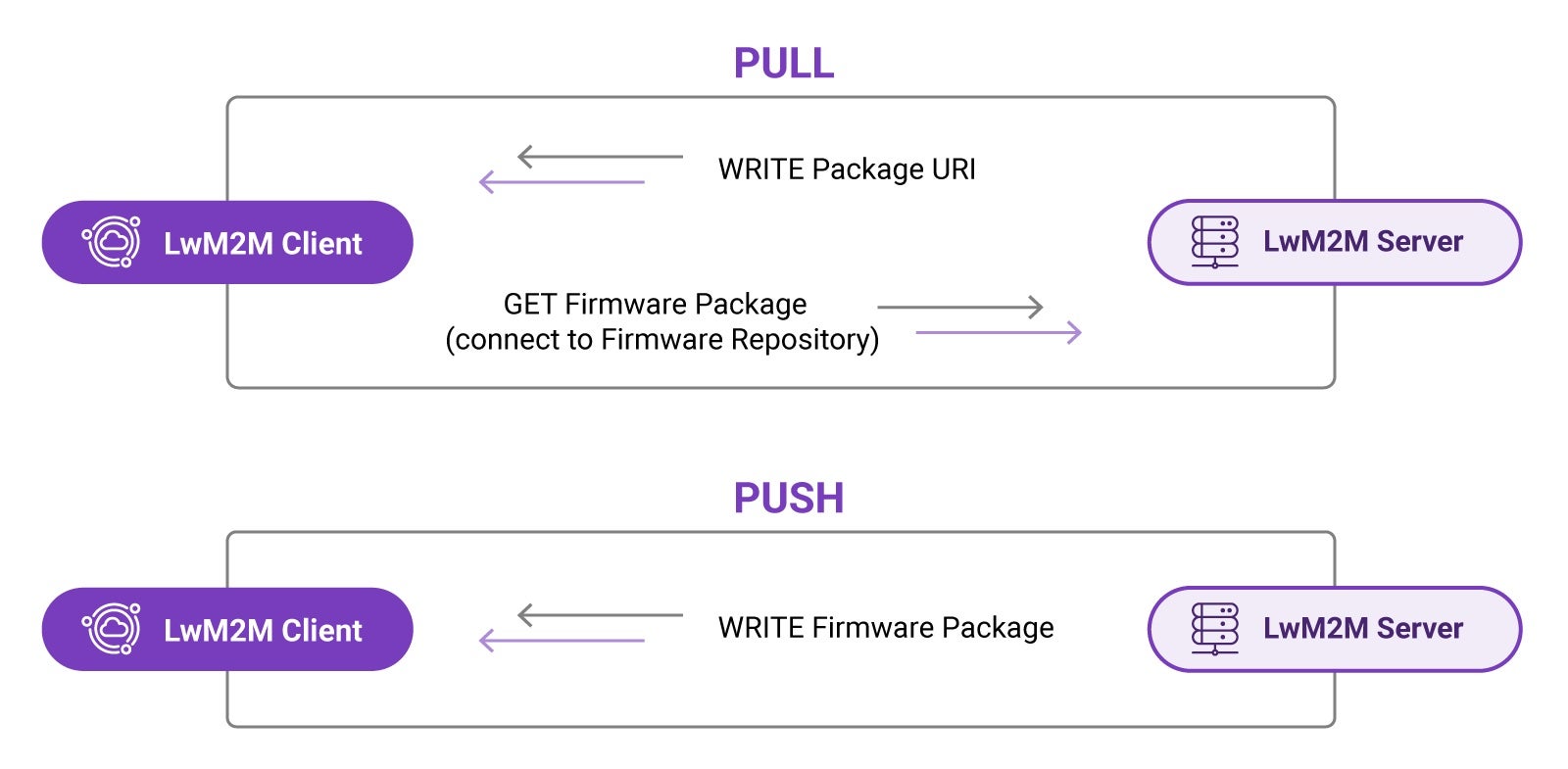
The LwM2M standard defines two methods to perform a firmware update, allowing either the Server or the Client to decide on the best moment to initiate the firmware download process.
The two methods are PULL and PUSH.
- PULL method: A device receives the location of the file that is to be downloaded and pulls the file from it.
- PUSH method: A LwM2M Server pushes the firmware file to the device.
PULL method
In the PULL scenario, the LwM2M Server provides the device with the address of the server containing the firmware file known as the Package URI. The device subsequently downloads the firmware from the so-called firmware repository at the earliest available opportunity.
PUSH method
In the PUSH scenario, the LwM2M Server determines the moment to initiate the firmware download, ideally based on the connectivity conditions. The device must have access to information such as Radio Signal Strength and Link Quality to support such server-side decision making. These resources are available in the LwM2M Connectivity Monitoring Object /4.
Firmware Delivery Methods
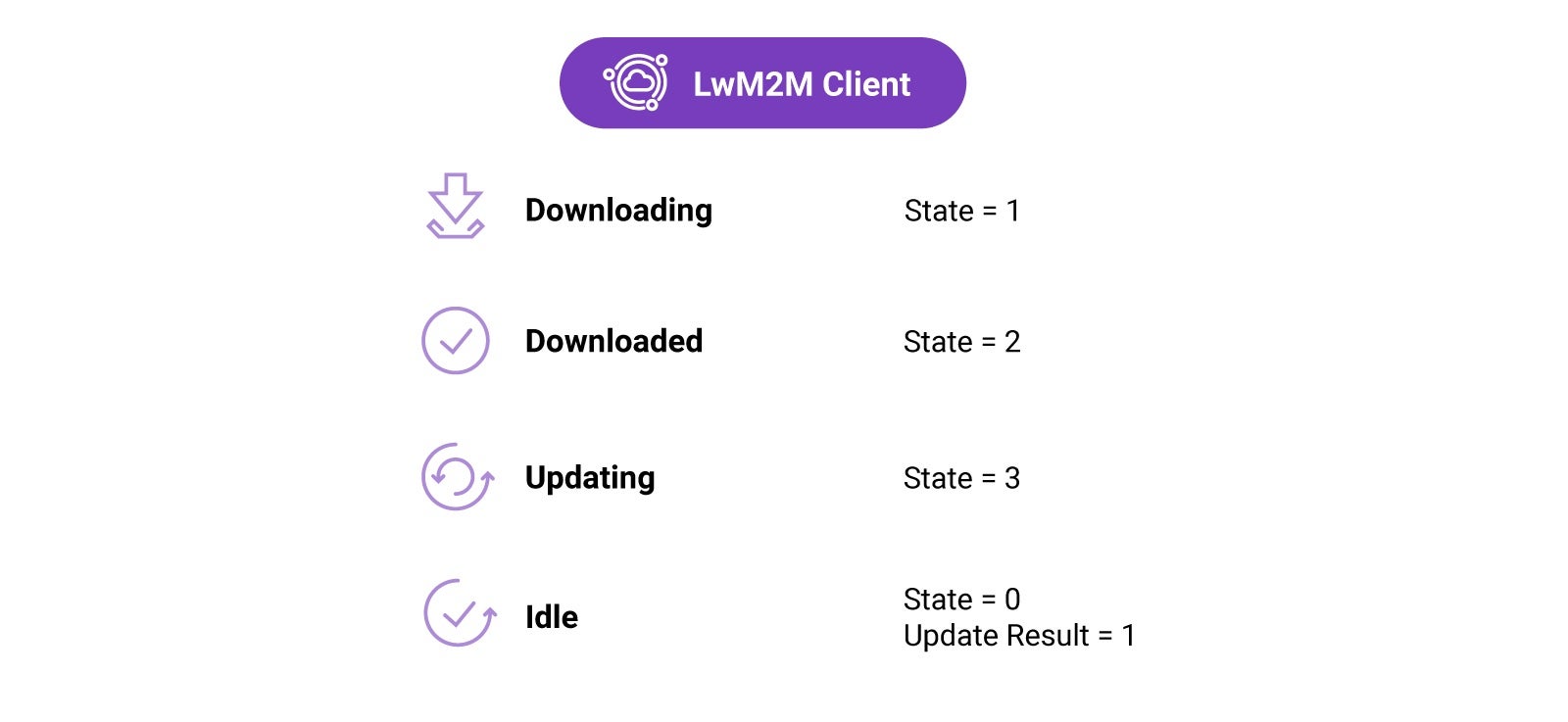
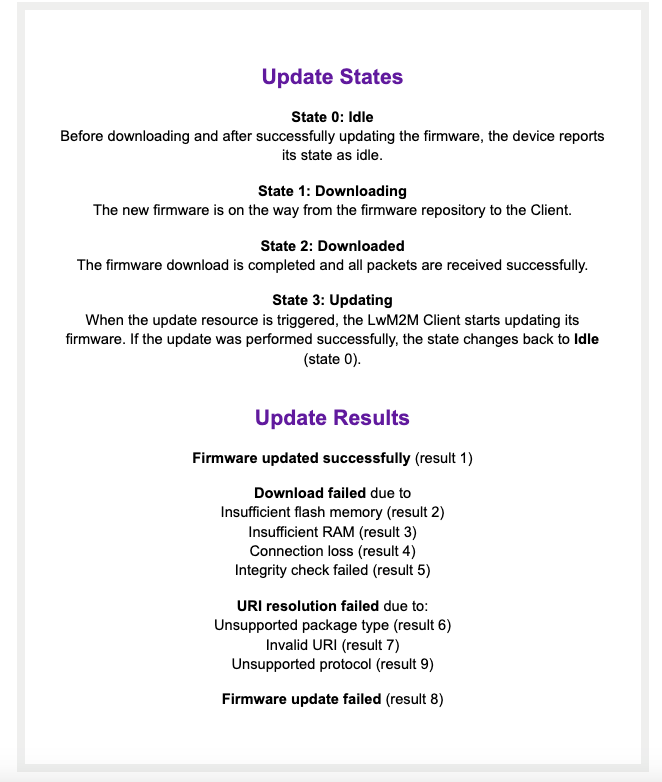
Firmware Update Object
The FOTA process is defined in the Firmware Update Object /5. This Object defines the update process using four states, as well as multiple update results representing the most common outcomes of the firmware update process.
Learn more about the Firmware Update Object on the OMA LwM2M Object and Resource Registry.
Firmware Update Process
Demonstration using the Zephyr’s LwM2M Client
Using Zephyr’s LwM2M Client, firmware can be updated over the air. In the below demonstration, new functionality is added to the Thingy:91 using LwM2M’s FOTA process.
[embedyt] https://www.youtube.com/watch?v=Lcsbd_UIzFg[/embedyt]
Conclusion
Remote IoT device updates are essential for the long-term success of IoT applications. Software bugs and security vulnerabilities will be found when deploying devices in the field which should be operational for years. As physical access to devices is often impossible to realize, FOTA is required for each, if not all IoT deployments.
Updating firmware remotely poses some serious challenges. Devices are constrained in terms of (flash) memory, battery capacity and available bandwidth, and often use unstable connections to the cloud. The LwM2M standard proposes a method to update the firmware of resource-constrained IoT devices. Through a structured approach with standardized states and error codes, developers can be assured that new firmware images can be safely sent to their fleet of devices in the field, regardless of hardware vendor or cloud platform used.
Learn more about LwM2M & FOTA
To learn more about LwM2M and FOTA, meet AVSystem in person at the Zephyr Developer Summit or join our upcoming webinar on July 12 about Firmware updates OTA.